In the realm of identity and access management, two terms keep coming up time and again: Identity Providers and Identity Service Providers. These terms might sound synonymous, yet the entities to which they refer are quite different and critical in securing and managing digital identities.
Understanding the difference between an IdP and an ISP is that understanding which every organization must have to implement a solid IAM. This article, therefore, discusses the definition, function, and differences of IdPs from ISPs and is going to let you take informed decisions as you put down your IAM strategy.
Identity Providers vs. Identity Service Providers Compared
Understanding Identity Providers (IdPs)
What is an Identity Provider?
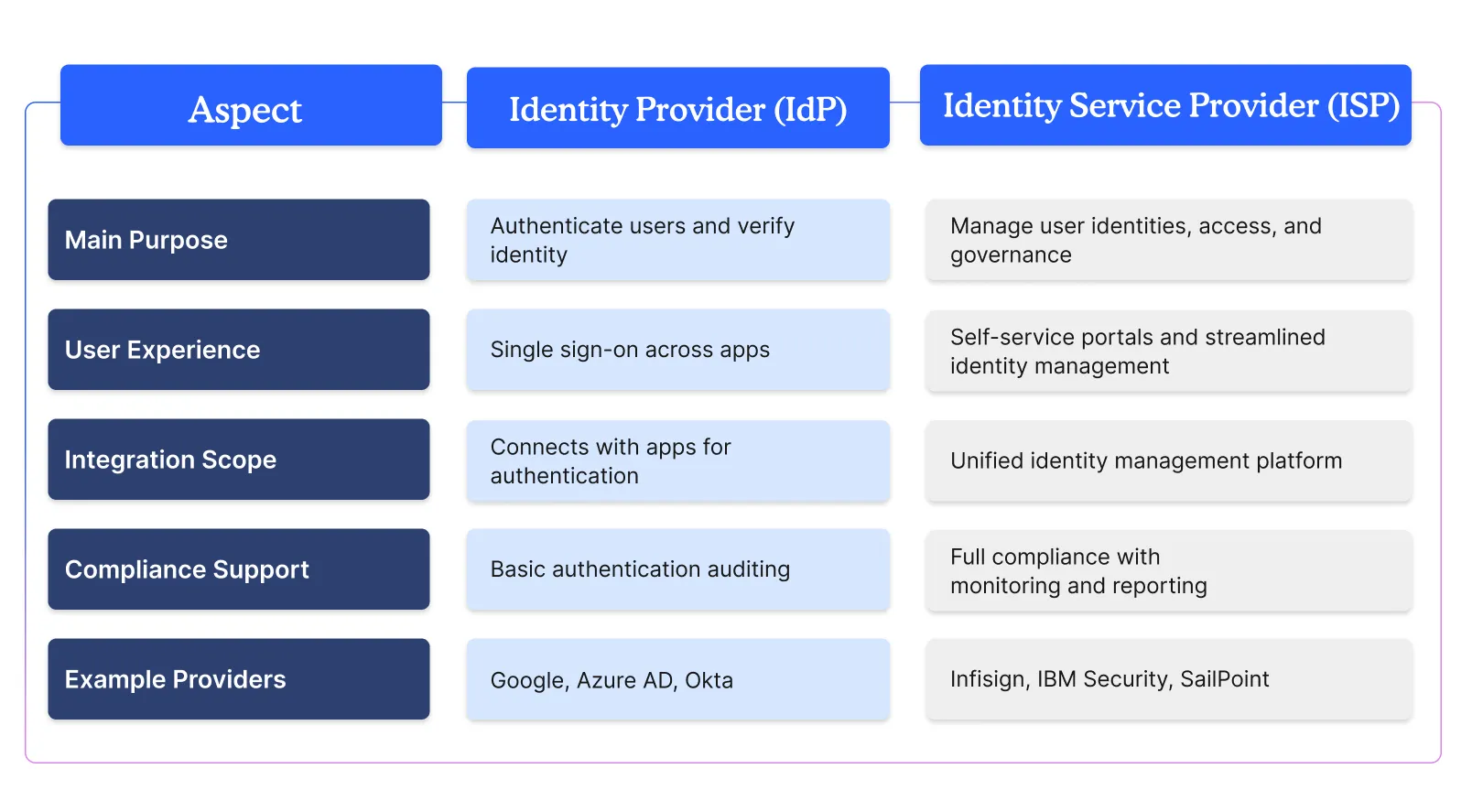
Identity Provider is a system that creates, maintains, and manages identity information. IdPs, at the same time, perform authentication services: they establish who a user claims to be and issue credentials.
Key Functions of Identity Providers:
- Authentication: End users are authenticated by the IdP in order to validate user's claims. This involves confirming the identity of someone who is trying to access a resource or service.
- Single Sign-On (SSO): A number of IdPs have features supporting single sign-on that assist end-users to log in only once, allowing them to get easy access to various applications or systems without reauthenticating.
- Federation: An IdP carries out identity federation in that it enables users to use their credentials across diverse domains or organizations to allow them seamless access to the resources.
Some Examples of Identity Providers
Some of the popular identity providers include Google, Microsoft Azure Active Directory, and Okta. These are the IdPs that establish secure access to applications and services.
Identity Service Providers (ISPs) – An Understanding
What is an Identity Service Provider?
An Identity Service Provider (ISP) provides a number of identity-related services that go beyond mere authentication. ISPs provide complete identity management services that encompass user provisioning and de-provisioning, access control, and also identity governance. They consolidate all the various identity services to develop one all-inclusive and secure IAM environment.
Roles of an Identity Service Provider
- User Provisioning and De-provisioning: An ISP holds the life cycle of a user identity in terms of creating, updating, and deleting of a user account from multiple systems and applications.
- Access Management: ISPs control the access to resources under a defined policy and user attributes that make sure access to sensitive information is only provided to authorized users.
- Identity Governance: Audit and monitoring activities involving the identity of users by ISPs are required by regulations and within the organization to comply with the desired outcomes.
- Self-Service Features: ISPS typically contain self-service portals that enable the users to reset their passwords, manage their profile, or request access to resources, thereby minimizing the administrative pressures on IT teams.
Examples of Identity Service Providers
Major examples of leading identity service providers are IBM Security Identity Governance and Intelligence, Infisign, SailPoint, and One Identity. These ISPS usually offer end-to-end identity management solutions that address various sectors of IAM.
Key Differences Between Identity Providers and Identity Service Providers
Scope of Services
The key difference between IdPs and ISPs lies in the scope of services they offer. While Identity Providers concentrate on the provision of authentication and access credentials, Identity Service Providers have a large range of services related to identity management, provisioning, access control, and governance. It normally enhances user experience because the IdPs allow users to sign in only once with access to a number of applications. The ISPs, as such, also give better user experience with self-service capabilities and hence are more effective, efficient, and automated in streamlining the processes of identity management.
Integration and Ecosystem with Other Applications and Services
Identity Providers usually have a lot of applications and other services integrated into them for providing authentication services. In contrast, Identity Service Providers bring in a number of identity services to make one single solution for managing identities across the organization.
ISP's Regulatory Compliance
They are placed with added capability to help organizations meet their regulatory compliance requirements. They offer monitoring, auditing, and reporting of identity-related activity to make sure the organization is in compliance with the internal policies and the external regulations.
Conclusion
Even though Identity Providers and Identity Service Providers have a major role in playing within the realm of identity and access management, there is a giant difference between two in terms of their functions and extent of those functions. Mainly, the concerns of Identity Providers are authentication and access credentials. They improve user experience by employing SSO and federation techniques, whereas Identity Service Providers take care of a larger view of user provisioning, access control, identity governance, and so forth.
At Infisign, we clearly understand the need for these two security components: IdPs and ISPs to secure digital identities. Our IAM suite is integrated with leading Identity Providers, providing robust authentication services while supporting comprehensive solutions for identity management in the role of an Identity Service Provider. With the Infisign IAM solution, your enterprise can have streamlined access control, increased security, and complete regulatory compliance—all to provide a fully effective and efficient IAM strategy. Check out the most important benefits of the integrated IAM solution for elevating identity management with Infisign.





















