With so many options available, choosing the right IAM platform can be challenging—especially when comparing Ping Identity and Okta. Both solutions offer strong features, but which one is a better fit for your security, scalability, and usability needs? In this Ping Identity vs Okta comparison, we’ll help you find the right choice for your business.
Ping Identity vs. Okta: A Detailed Comparison
What is Ping Identity?
Ping Identity is one of the more popular cloud-based identity and access management (IAM) providers. With single sign-on (SSO), multi-factor authentication (MFA), and directory it helps secure access to applications and APIs. Ping helps organizations manage user identities and control access to resources across hybrid IT environments.

Pros and Cons of Ping Identity
- Centralized Access Governance: Ping Identity streamlines access management by consolidating control over applications and systems into a single, unified platform. This centralized approach also simplifies regulatory compliance efforts for organizations.
- Offline Multi-Factor Authentication: The platform's multi-factor authentication (MFA) capabilities function even without an internet connection, ensuring secure access in remote or offline scenarios. This is particularly valuable for industries where uninterrupted access to critical systems is paramount.
- API-Driven Integration: Ping Identity's support for API integrations facilitates seamless connectivity across a wide range of applications and ecosystems. This adaptability empowers administrators to optimize workflows, easily integrate new tools, and scale operations efficiently.
- Smooth Login with Single Sign-On: Single Sign-On (SSO) improves user experience by enabling swift and secure access to multiple applications with a single login. This minimizes password management issues, reduces login times, and strengthens overall security.
Cons and Challenges of Using Ping Identity
- Slow Technical Support: Ping Identity's technical support can sometimes be slow or ineffective, potentially delaying the resolution of critical issues. This can be problematic when rapid assistance is essential for maintaining business operations.
- Synchronization and Notification Challenges: Delays in synchronization and push notifications can disrupt workflows and impact the effectiveness of access management. For example, delayed notifications can hinder timely approvals or critical updates.
- Complex Configuration and Deployment: Setting up Ping Identity can be a complex undertaking, requiring significant time and specialized knowledge for proper configuration. This complexity can extend deployment timelines and potentially increase costs associated with consulting services.
- Limitations with Custom Attribute Configuration via OIDC: Configuring custom attributes using OpenID Connect (OIDC) can be challenging, potentially restricting the platform's ability to address specific requirements. This can be a hurdle for organizations with unique identity management needs.
What is Okta?
Okta is a cloud-based identity and access management (IAM) platform that helps organizations securely manage user access to applications and resources.
This IAM software has single sign-on (SSO), multi-factor authentication (MFA), and lifecycle management for its users. Aside from this, Okta also works with various cloud and on-premises applications, simplifying user administration and enhancing security.

Pros and Cons of Okta
Pros or Advantages of Using Okta
- One Login for Many Apps: Okta's Single Sign-On (SSO) lets users access multiple applications with just one login, getting rid of the hassle of remembering many different passwords. This makes getting into applications much easier.
- Stronger Security: Okta boosts security with things like Two-Factor Authentication (2FA) and Adaptive Multi-Factor Authentication (MFA). These methods require extra verification steps, such as a code sent to a phone or a fingerprint scan, in addition to a password.
- Controlling Access: Okta helps businesses manage who can see what data. It gives companies the tools to oversee and control access to applications and data, keeping private information secure and making sure employees only have access to what they need for their jobs.
- Meeting Data Compliance Rules: Okta helps businesses meet data privacy rules. It offers tools for managing access, keeping track of who views what, and setting rules for data storage, so companies can follow strict data protection laws.
Cons and Challenges of Using Okta
- Getting Started: Setting up and running Okta, which has lots of features, can be tough, especially if a company doesn't have a dedicated IT department.
- App Support: Okta works best with apps that support Single Sign-On (SSO). Older or custom-made apps might not work perfectly with it, which could limit its usefulness.
- Extra Security Costs: Some of Okta's more advanced security features, like using fingerprints or face recognition to log in, cost extra. Businesses have to decide if these added features are worth the extra money.
- Using on Multiple Devices: Using Okta on several devices can be tricky. People who use different devices, like laptops, phones, and tablets, might have trouble keeping everything in sync, and logging in on different devices might involve extra steps, which can be annoying if it's not set up correctly.
Ping Identity vs. Okta: A Detailed Key Feature Comparison
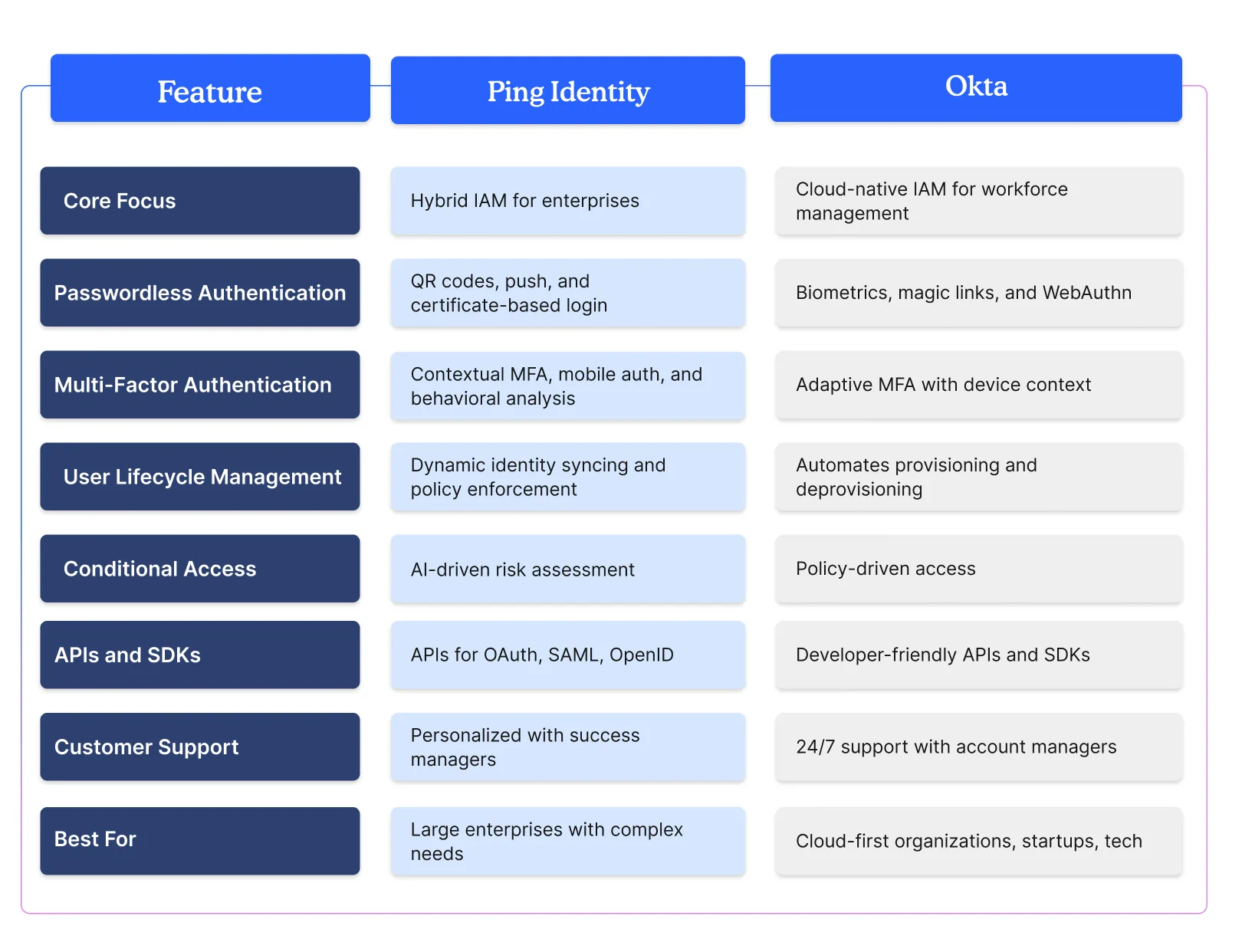
1. Passwordless Authentication
Passwordless authentication eliminates the need for remembering passwords, offering a smoother and more secure login experience. Both Ping Identity and Okta make it easier to securely access your applications without traditional passwords.
- Ping Identity also supports passwordless authentication, with adaptive authentication policies, enabling organizations to transition users to stronger authentication methods such as QR code login, push notifications, and certificate-based authentication.
- Okta enables passwordless authentication through options like biometrics, FIDO2 WebAuthn, and email-based magic links. These methods reduce reliance on traditional passwords while improving both security and user experience.
2. User Lifecycle Management
Managing user access from onboarding to offboarding is essential for both security and compliance. Ping Identity and Okta are strong tools that help businesses manage user lifecycles efficiently, ensuring that access is granted, updated, or revoked based on role changes and employment status.
- Ping Identity offers flexible user lifecycle management capabilities, syncing identities across multiple directories. Its workflows help organizations enforce access policies dynamically as user roles evolve.
- Okta automates user provisioning and deprovisioning through deep integrations with HR systems and cloud applications. Its identity lifecycle policies ensure that users always have the right level of access.
3. Multifactor Authentication (MFA)
For multifactor authentication (MFA), enhancing security while keeping the user experience smooth is key. Both Ping Identity and Okta offer powerful MFA features, ensuring that access remains secure without slowing down the workflow.
- Ping Identity provides a comprehensive MFA solution with contextual authentication policies that assess risk in real time. It supports step-up authentication using mobile authenticators, hardware tokens, and behavioral analytics.
- Okta’s adaptive MFA engine evaluates multiple risk signals, such as device context and geolocation, before prompting users for an additional authentication factor. Its support for push notifications, security keys, and biometrics strengthens security without disrupting productivity.
4. Conditional Access
Conditional access helps define who can access what based on user behavior and device security. Ping Identity and Okta both offer strong conditional access features, ensuring secure and dynamic control over access.
- Ping Identity delivers advanced conditional access capabilities with policy enforcement at the application level. Its AI-driven risk assessment dynamically adapts access decisions based on context, reducing friction for low-risk users while tightening security for high-risk scenarios.
- Okta’s policy-driven conditional access framework enables fine-grained control over authentication and authorization. Security teams can define rules based on user behavior, device compliance, and real-time threat intelligence.
5. APIs and SDKs
For smooth integration of authentication into your apps, both Ping Identity and Okta Ping Identity offer reliable APIs and SDKs:
- Ping Identity has API security capabilities with a focus on standards like OAuth, OpenID Connect, and SAML. Developers can use Ping’s SDKs to embed authentication directly into applications while ensuring compliance with enterprise security requirements.
- Okta provides a wide range of developer-friendly APIs and SDKs that simplify authentication, authorization, and user management across web and mobile applications. Its RESTful APIs support granular policy control, allowing businesses to define security rules at scale.
6. Customer Support
- Ping Identity, on the other hand, has personalized customer support with dedicated success managers for large deployments. It provides in-depth documentation, training programs, and an active user community to assist with complex identity challenges.
- Okta provides 24/7 customer support with multiple tiers, including dedicated account managers for enterprise clients. Its online knowledge base and developer community offer extensive resources for troubleshooting and best practices.
Why Infisign is the Perfect Alternative to Ping Identity and Okta
Infisign’s IAM Suite offers a modern, zero-trust IAM solution for both cloud and hybrid ecosystems. With passwordless SSO, adaptive MFA, and conditional access, it simplifies access management while ensuring strong security.
What sets Infisign apart? Unlike other platforms, it allows admins to grant access instantly via Slack or Teams, streamlining workflows. With automated provisioning and over 6000+ app integrations, it saves time and strengthens security.
Key Features of Infisign:
- Adaptive Multi-Factor Authentication (MFA) with SMS, email, and app-based tokens.
- User Federation with SSO for seamless sign-ons across platforms.
- Attribute-Based Access Control (ABAC) to grant access based on department, email, and more.
- Zero Trust Security that continuously verifies users, ensuring secure access.
- Network Access Gateway (NAG) for smooth integration with on-premises applications.
- Conditional Access based on user location, device, or IP.
- Real-time IT Access Review through Slack/Teams, with automation options.
- Over 6000 app integrations for seamless access to your existing tools.
- Passwordless authentication using Zero Knowledge Proof to enhance security.
With its modern, API-first approach, Infisign offers a seamless solution for businesses looking for a scalable, secure, and easy-to-use IAM platform. Whether you're looking to manage cloud-native or on-premises architecture, Infisign is the perfect solution that scales with your business needs. Want to see how it works? Reach out for a free trial!






















