Your business faces real cyber threats every second. Hackers target companies like yours daily. Traditional passwords fail constantly. Smart businesses use multi factor authentication software to stay protected.
We tested every major solution to find what works. These tools protect billions of users worldwide daily. Each offers unique power for different business needs. Choose wrong, and you risk everything you built. Modern cyber threats bypass traditional MFA through sophisticated techniques like prompt bombing, session token theft, and AI-powered phishing attacks.
Your survival depends on this decision alone today. Make it count.
Top Multi-factor Authentication (MFA) Software: A Detailed Comparison
What is Multi-factor Authentication Software?
Multi-factor authentication requires two or more identity proofs before granting access. Think of it as multiple locks on your digital door.
MFA software uses three main types:
- Something you know: Passwords or PINs
- Something you have: Phone or safety key
- Something you are: Fingerprints or face scan
Normal login uses just passwords. MFA adds extra safety steps. Even if hackers steal your password, they cannot access your accounts. They need your phone or fingerprint too.
Modern MFA software helps businesses control access completely. It protects both office and cloud systems. Your team stays safe while working efficiently.
10 Top Multi-factor Authentication (MFA) Software Solutions in 2025
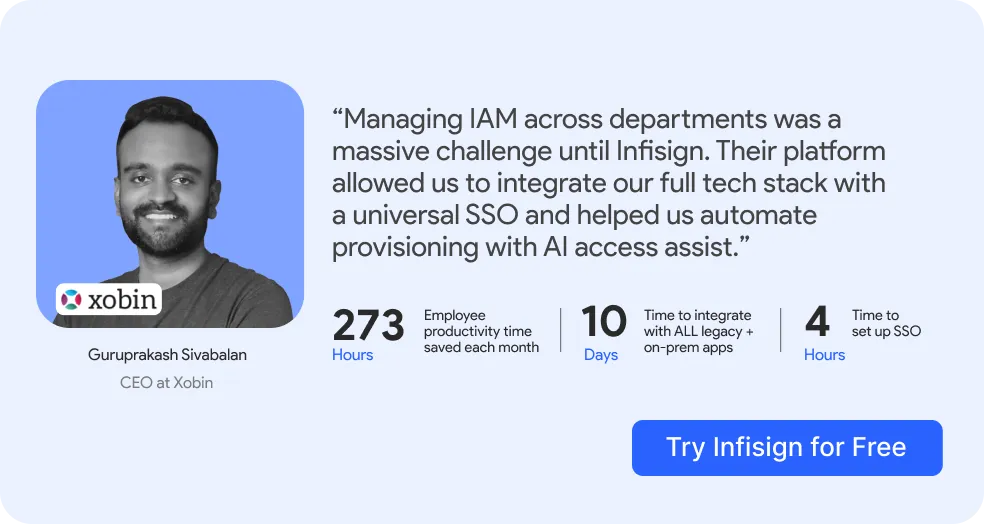
1. Infisign
Infisign is the next generation of identity and access management tech built on Zero Trust and powered by AI. This complete platform changes how you secure your digital systems. Unlike old MFA software that just adds login layers, Infisign creates a complete safety framework built on a zero-trust model. It adapts, learns, and grows with your business needs.
Key Features:
- 4-Hour Complete SSO Setup. Infisign sets up your entire SSO in under 4 hours with 6000+ ready-made connections. The platform gives you Universal Single Sign-On with Network Gateway tech that lets you access old on-site apps through cloud setup. Legacy apps without SAML support work perfectly through MPWA technology. You don't need expensive upgrades to secure old systems.
- AI-Powered Smart MFA System. The system uses machine learning to watch user behavior patterns and check device health, location data, and threat intelligence. Smart MFA changes security needs in real-time - low-risk logins get easy access while suspicious activities get extra checking. The AI learns from user behaviors and gets better through behavioral learning and strange activity detection. Supports adaptable MFA like magic links, biometrics, OTPs, push notifications, and passkeys that can be changed based on conditions you set with conditional access control.
- Passwordless Authentication Methods. This supports magic links, OTPs, biometrics, device passkeys, and QR codes completely. It removes risks like ransomware, phishing, and hacked accounts from your business. Users never remember passwords again while staying more secure than traditional methods.
- AI Access Helper with Workflow Automation. This runs access approvals through Slack, Teams, or AI interfaces automatically. Your custom rules handle complex decisions without human input. Zero manual work needed for standard user access requests. This saves your IT team hours daily while maintaining strict security controls.
- Smart Access Control with ABAC Technology. Infisign uses attribute-based access control for detailed permissions based on user features like job role, department, or project. Just-in-time access gives temporary high privileges only when needed. It follows least privilege rules with full audit trails so teams get exactly what they need when they need it.
- Non-Human Identity Management for Bots and Systems. This manages workforce productivity and customer sign-ups through automated identity management. AI interfaces handle machine identities and automated access for better control. Your bots, APIs, and automated systems get secure access with the same level of protection as human users.
- Built-in Compliance and Audit Support. This tracks and manages safety rules meeting GDPR, HIPAA, SOC 2 requirements automatically. You get instant audit readiness with automatic activity records and data compliance built-in. Auditors get everything they need without extra work from your team or expensive consulting.
- Complete User Lifecycle Management System. This handles user provisioning and deprovisioning with user onboarding and offboarding done through a few clicks. It adds or removes users from multiple tools automatically based on your set rules. New hires get access on day one, departing employees lose access immediately with zero security gaps.
Pros:
- Fast setup gets you secure in four hours not months
- Smart AI learns your team work style for easy access
- All security tools work together in one simple platform
Cons:
- Passwordless authentication requires password vault migration during initial setup.
2. Okta Adaptive MFA
Okta Adaptive MFA keeps access safe across all places. This includes cloud, office, and mobile systems. It uses smart risk checking to change safety needs. The system looks at user and device details by itself. This multi-factor authentication solution works with many business apps.

Key Features:
- Wide App Support. Works with thousands of business apps through built-in links. No custom coding or setup time needed for most connections
- Multiple Login Options. Gives you body scans, SMS, voice, email, and physical tokens. Users pick their liked login method from available choices
- Smart Risk Detection. Changes safety needs based on bad activities it finds by itself. Balances safety with user ease in a perfect way
- Device Protection. Makes MFA safety reach all your devices through RADIUS connection. Includes VPNs and network access points for complete coverage
- Performance Scaling. Gives detailed safety reports and grows from small teams to large companies. Keeps steady performance levels as you expand
Pros:
- Lots of ready made app connections save setup time
- Proven system that big companies trust and use daily
- Smart risk checking stops attacks before they can start
Cons:
- Costs a lot per user every month for teams
- Takes three to six months to set everything up
- Must pay big fees upfront even for small companies
3. Auth0
Auth0 is a leading customer identity and access management provider perfect for businesses of all sizes. It simplifies login and permission management for developers. Auth0 excels for companies wanting flexible MFA software solutions. The platform adapts to each login attempt's risk level. This mfa solution provider offers powerful features.
Key Features:
- Smart Risk Scoring. Figures out trust scores based on risk checks. Uses device finding and location checks by itself for you
- Push Message System. Send push messages to your signed-up devices for instant approval. Users can deny with just one tap
- One-Time Password Creation. Make safe one-time passwords through login apps you already use. Works with Google or Microsoft Login apps daily
- WebAuthn Support. Supports WebAuthn with safety keys and body scan device login. Gives password-free access that users love most to use
- High Availability. Grows easily with millions of daily logins and promises uptime. Gives reliable business work always without downtime issues
Pros:
- Easy for coders to customize and build on quickly
- Free plan lets you try before paying anything at all
- Grows with your business without huge upfront costs ever
Cons:
- Hard setup needs tech experts to do it right
- Gets expensive fast when more people use it regularly
- Missing some business tools that big companies need daily
4. Microsoft Entra ID
Microsoft Entra ID offers complete identity management with MFA. It was formerly called Azure AD before the name change. The system needs two or more login methods for safety. It works best with other Microsoft products and services.
Key Features:
- Microsoft Integration. Supports Windows Hello, Microsoft Login, and FIDO2 safety keys. Works seamlessly across all Microsoft ecosystem products without setup
- Conditional Access Rules. Uses conditional access rules that change to threats by itself. Based on user location, device, and behavior patterns
- No Setup Needed. Works perfectly with Microsoft 365 and Azure services. No additional setup or setup time needed for basic functions
- Fraud Detection. Includes built-in fraud alerts and login checking you need. Detects suspicious login tries before damage happens to accounts
- Cost Savings. Saves your group average $250,000 yearly in IT costs. Cuts password-related help desk support tickets by 80% every year perfectly with Microsoft ecosystem products
Pros:
- Works perfectly with Microsoft Office and Windows systems everywhere
- Can save two hundred fifty thousand dollars per year
- Built in rules help you follow legal compliance requirements
Cons:
- Does not work well with Apple or Android tools
- Pricing plans are confusing with hidden expensive features always
- Interface changes often making it hard for admins to learn
5. Google Authenticator
Google Authenticator is a free app for two-factor authentication. Google developed this software-based authenticator. The biggest update is cloud syncing across devices. This app generates time-based security codes.
Key Features:
- Password Generation. Creates six to eight-digit one-time passwords. Refreshes every 30 seconds for safe account access and maximum security protection
- Multiple Account Management. Manages many accounts in a single app interface. You control all your 2FA codes from one easy place without switching apps
- Cloud Backup System. Cloud backup syncs to your Google account across all devices. Stops lockouts when you upgrade phones or lose devices completely
- Privacy Screen Protection. Uses your device lock, PIN, or body login methods. Protects the app itself from unwanted access by unauthorized people
- Offline Operation Support. Works without internet connection making verification codes offline. You always have access when needed most without network requirements
Pros:
- Free app with no monthly costs for basic security
- Easy setup that anyone can learn in few minutes only
- Works without internet so you are never locked out completely
Cons:
- Only basic features without smart threat detection tools available
- No admin controls for managing company wide security policies
- Cannot connect with business systems for centralized management ever
6. Duo Security
Cisco Duo protects access across all places safely. Duo gives strong safety without hard setup work. It works with apps, data, and mobile systems. The enterprise mfa solutions change to user behavior and location.
Key Features:
- Multiple Login Methods. Duo Push, WebAuthn, body scans, tokens, and passcodes available. Gives users many easy choices for safe login daily
- Context-Based Safety. Smart login changes based on user context like location. Uses device health and behavior patterns by itself
- Password-Free Login. Makes logins simpler while keeping safety through body checks. Uses hardware tokens you trust for access
- Device Health Checks. Checks safety status before giving access to protect. Stops compromised endpoints and bad software from getting in
- Threat Detection System. Real-time threat finding responds to suspicious activities instantly. Blocks attacks before they cause damage to important systems
Pros:
- Easy deployment and management with minimal IT overhead requirements
- Strong device health monitoring prevents compromised endpoints from accessing systems
- Balanced approach between security and user experience for mid-size organizations
Cons:
- Limited advanced analytics compared to enterprise-focused platforms like Okta
- Fewer customization options for complex authentication workflows and policies
- Less suitable for large enterprises needing extensive integration and governance capabilities
7. CyberArk
CyberArk Multi-Factor Authentication keeps attackers out completely. It keeps your entire group's digital assets safe. This includes apps, VPNs, workstations, and endpoints. The system uses smart behavior checking for safety.
Key Features:
- Context-Based Challenges. Uses behavior signals and past patterns. Finds unusual activities by itself for you
- Multiple Login Methods. Many login methods include password-free choices. Physical tokens and body checks for maximum safety flexibility
- Pattern Analysis System. Compares current access requests against normal user behavior. Identifies possible threats before they cause problems
- REST API Integration. Lets you put custom MFA workflows in your existing apps. Gives you full control over the setup process
- Endpoint Protection. Advanced endpoint protection keeps desktop computers safe. Mobile devices against login-based attacks and bad software threats
Pros:
- Strong PAM access capabilities protect critical administrative accounts
- Advanced behavioral analytics detect sophisticated insider threats and anomalous activities
- Comprehensive endpoint protection extends security beyond authentication to device level
Cons:
- Complex implementation requiring specialized expertise and extensive planning phases
- High pricing model targeting enterprise customers with substantial security budgets
- Steep learning curve for administrative teams managing advanced privileged access features
8. LastPass MFA
LastPass combines password management with strong multi factor authentication software features. It manages passwords safely while offering login checking. This complete tool serves both safety needs together well. The platform focuses on user ease and simple setup.
Key Features:
- Mobile Push and Body Checks. Work together for safe yet easy login you can trust. Uses advanced body checking tech for smooth access
- Smart Login Combination. Combines many safety factors by itself based on risk levels. Uses user access patterns to make smart choices
- Unified Admin Console. Manages both password policies and MFA settings. One central dashboard for easier control over all safety settings
- Safe Password Vault. Uses local device encryption to protect stored login details. Syncs across all devices while keeping everything safe
- Wide Business Connections. Works with VPNs, identity providers, and apps. Gives complete safety coverage everywhere you work
Pros:
- Unified solution combining password management and MFA reduces complexity
- User-friendly interface with streamlined setup process for quick deployment
- Cost-effective option providing both password storage and authentication in one platform
Cons:
- Less advanced MFA features compared to dedicated authentication platforms
- Limited enterprise-grade reporting and analytics capabilities for large organizations
- Dependency on single vendor for both password management and authentication security
9. Ping Identity
Ping Identity offers MFA within a complete identity platform. This best mfa solutions works for hybrid and multi-cloud setups. It enables safe access across different devices and systems. The platform focuses on user experience balance and smooth operation.
Key Features:
- Flexible Login Methods. Mobile push, body scans, FIDO2, and more login methods available. Gives users flexible choices for safe access
- Smart Policy System. Consider context and risk levels by itself. Minimizes user friction while keeping strong safety standards
- Administrative Dashboards. Gives detailed usage insights and cost analysis. Helps you optimize your safety investments over time
- Password-Free Access. Improves user experience while giving stronger safety. Better than old password-based methods you know
- Global Scale Support. Handles millions of users with steady performance. Reliability across all geographic regions without slowdown
Pros:
- Enterprise-grade platform handling millions of users with consistent performance
- Comprehensive identity management beyond basic MFA including advanced governance features
- Strong support for hybrid and multi-cloud environments with flexible deployment options
Cons:
- Complex pricing structure making cost predictions challenging for budget planning
- Requires significant implementation expertise for proper configuration and optimization
- May be overpowered for small to medium businesses needing basic authentication features
10. IBM Verify
IBM Verify gives advanced mfa software and password-free login. It includes smart access policies and AI insights for better safety. The platform offers complete identity management features. It changes to different risk levels by itself.
Key Features:
- Multiple Login Options. IBM Verify app, login apps, TOTP, email and SMS choices. Gives you many safe login choices to pick from
- QR Code and Security Keys. QR code login and FIDO2 safety keys enable password-free access. Users prefer these over old methods
- Smart Policy Adjustment. Login policies adjust MFA needs by itself. Based on contextual risk factors like location and device
- Detailed Reporting System. Helps administrators watch deployment success. Optimize safety policies for better user experience
- Wide Platform Support. Works with diverse apps, databases, and IT systems. Gives complete safety coverage for all your needs
Pros:
- Comprehensive platform supporting both IAM and CIAM use cases
- AI-powered adaptive access using IBM Trusteer technology for advanced threat detection
- Strong enterprise scalability handling millions of user accounts effectively
Cons:
- Complex setup process with steep learning curve requiring technical expertise
- User interface feels outdated compared to modern alternatives
- Mobile app performance issues affecting user experience and adoption
Why do you need Multi-factor Authentication (MFA) software?
Cyber threats get stronger and smarter every day. Safety must be your top business focus now. Password safety alone doesn't work against new attacks. Hackers use smart methods like fake emails and login stealing.
Understanding MFA in cyber security helps you protect against modern threats. The right multi factor authentication vendors provide complete protection for your business data.
Key Reasons You Need multi factor authentication vendors Today:
- Data breaks cost businesses millions in fix costs. They also hurt customer trust and company name. A multi-factor authentication solution makes unwanted access much harder for criminals. Even stolen passwords can't get hackers inside.
- A single data break costs companies $4.45 million on average. MFA stops 99.9% of robot cyber attacks. Your money pays for itself quickly.
- Meets Legal Rule Needs Healthcare, finance, and government have strict safety rules. HIPAA, PCI-DSS, and GDPR need strong login checking. MFA helps you meet these legal standards. Avoid costly fines and legal problems.
- Rule breaks can cost $10 million or more. MFA makes checks much easier to pass. You keep both data and business names safe.
- Cuts Password-Related Problems Passwords cause most safety issues in business. People use weak passwords across many accounts. They write passwords down or share them with others. MFA cuts passwords a lot. Passwordless MFA eliminates these vulnerabilities completely.
- Password resets cost $70 per ticket average. MFA cuts these costs by 80% or more. IT teams spend time on important work instead.
- Protects Against Modern Attack Methods Criminals use smart phishing and social engineering attacks. They steal passwords through fake websites and emails. Even with stolen passwords, MFA blocks access. Hackers need physical devices or biometric data.
- Phishing attacks succeed 30% of the time without MFA. With MFA, the success rate drops below 1%. This protection is essential for business survival.
Additional Security Benefits:
- Protects remote workers on any device
- Secures cloud applications and data storage
- Monitors suspicious login attempts automatically
- Provides detailed audit trails for investigations
- Reduces cyber insurance premiums significantly
- Builds customer confidence in your security
How to choose the perfect multi-factor authentication (MFA) vendor?
Picking the right MFA solution needs careful planning. Here are key things for smart choices:
Connection Abilities.
Look for prebuilt links with your current apps. Test all connections before making final choices. Check if APIs work with custom software. Make sure setup doesn't break existing systems.
Consider advanced authentication methods that work with your business needs. The best IAM software offers multiple integration options for different systems.
Ask these questions:
- Does it work with our email system?
- Can it link to our HR database?
- Will it sync with cloud apps?
- Does it support our VPN setup?
User Experience Quality.
Simple interfaces improve worker adoption rates a lot. Hard systems create pushback and safety gaps. Test the user journey from start to finish. Make sure the login process stays fast and easy.
Good user experience means:
- Clear setup guides help all workers understand the system quickly.
- Fast login processes don't slow down daily work activities.
- Multiple authentication choices accommodate different user preferences.
- Help documentation should be accessible for anyone to understand easily.
Many Login Choices.
Different people prefer different safety methods. Some like phone apps, others prefer hardware keys. The best solutions offer many choices. This flexibility improves adoption and happiness.
Think about these login types:
- SMS text messages to mobile phones
- Login apps like Google or Microsoft
- Hardware tokens or safety keys
- Body scans like fingerprints or faces
- Push messages to signed-up devices
Scalability for Business Growth.
Your security needs will change as business grows. Choose solutions that scale with your company. Check pricing models for different user numbers. Make sure performance stays good with more users.
Growth considerations include:
- Important growth considerations include system capacity for 10x more users.
- Pricing should stay reasonable at scale without hidden costs.
- Performance must not slow with increased traffic volume.
- The system should work across multiple locations seamlessly.
Strong Security Standards.
Security vendors must follow industry best practices. Check for relevant certifications and compliance standards. Make sure they update software regularly. Ask about their security track record.
Look for these certifications:
- SOC 2 Type II compliance
- ISO 27001 security standards
- FIPS 140-2 encryption requirements
- Industry-specific compliance when needed
Quality Support Services.
Good support helps during problems and questions. Check response times for different issue types. Look for multiple support channels like phone and chat. Read reviews about their support quality.
Support features to evaluate:
- 24/7 availability for critical issues
- Multiple contact methods available
- Good documentation and training resources
- Fast response times for urgent problems
Transparent Cost Structure.
Understanding total costs includes evaluating all hidden fees carefully. Some charge per user while others charge per tenant. Include setup implementation training and ongoing maintenance costs completely. Calculate return on investment over multiple years accurately.
Cost factors include:
- Monthly or yearly subscription fees
- Setup and implementation costs
- Training expenses for IT team
- Ongoing maintenance and support
Secure Every Login with Infisign
Transform your organization's security posture with the most advanced identity and access management platform available today. Infisign doesn't just protect your data - it revolutionizes how your team works, dramatically reducing complexity while strengthening security beyond traditional limitations.
Why Organizations Choose Infisign Over All Alternatives:
- Revolutionary Technology Foundation. Experience the future of cybersecurity through AI-powered automation, decentralized identity management, and Zero Knowledge Proofs that make traditional password breaches impossible. Our platform learns from every interaction, continuously improving protection while eliminating the security gaps that plague conventional solutions.
- Complete Business Transformation. Stop managing scattered security tools. Infisign's UniFed IAM Suite combines IAM, CIAM, MFA, SSO, and access controls into one smart platform. Your IT team saves 40+ hours weekly while employees get easy, secure access to everything they need. The platform provides comprehensive Identity and governance capabilities to manage user access throughout their entire lifecycle.
- Unmatched Cost Efficiency. Our tenant-based pricing model grows with your success, not your headcount. While competitors charge thousands per user annually, Infisign provides enterprise-grade security at startup-friendly prices. Directory sync, passkey authentication, and advanced features come standard - no hidden fees or surprise upgrades required.
- Instant Implementation Success. Deploy comprehensive security with SSO setup in under 4 hours instead of months. Our pre-built integrations connect with 6000+ applications automatically, and our team creates custom integrations for your unique requirements. Zero downtime, zero disruption, maximum protection from day one. Experience how to automate user lifecycle management with intelligent workflows.
- Future-Proof Architecture. Built for tomorrow's threats and today's hybrid workforce challenges. As cyber attacks evolve, Infisign adapts automatically through machine learning algorithms that stay ahead of emerging risks. Your security investment protects your organization for years, not just months.
Ready for Top-Tier MFA Protection?
Unlike basic authenticator apps, Infisign's UniFed IAM Suite delivers adaptive mfa setup with real experts guiding your implementation. Experience seamless security across all platforms. Get your free trial today. Book Your Free Demo Today!
FAQs
What is the best MFA solution?
The best MFA solution depends on your specific needs. Modern companies need smart, changeable safety systems. Look for solutions with AI-powered risk checking. Choose platforms that work with existing systems. The top choice offers many login methods at good prices.
What is the most commonly used MFA?
SMS codes and login apps are most popular. Google Login has millions of users worldwide. However, SMS messages can be caught by criminals. Login apps give better safety than SMS. Push messages are becoming more popular choices.
What is MFA authentication?
MFA login needs two or more identity proofs. Users must give many check types. This might include passwords, phone codes, and fingerprints. The system checks all proofs before giving access. This process stops most cyber attacks.
What are the benefits of using MFA?
- Better Safety Protection: MFA blocks unwanted access even with stolen passwords. It stops 99.9% of robot cyber attacks. Your sensitive data stays safe from criminals.
- Legal Rule Support: MFA helps meet industry safety needs. It satisfies HIPAA, PCI DSS, and GDPR standards. You avoid expensive rule breaks and fines.
- Fewer Password Problems: MFA cuts passwords a lot. IT teams handle 80% fewer password reset requests. Workers spend less time on access issues.
- Lower Safety Costs: Companies save 50-65% on login expenses. Password reset tickets cost $70 each average. MFA almost gets rid of these expensive support calls.






















